This module exploits a sqli vulnerability found in openemr version 5. 0. 1 patch 6 and lower. the vulnerability allows the contents of the entire database (with exception of log and task tables) to be. Security advisory with all the details about a critical sql injection in openemr web application discovered by netsparker web vulnerability scanner. Openemr 4. 1. 1 patch 14 sql injection / privilege escalation / remote code execution (metasploit). cve-97482. remote exploit for php platform. This module exploits a sqli vulnerability found in openemr version 5. 0. 1 patch 6 and lower.
Openemr sql injection: reference 2: video poc for openemr exploitation. with the above reference, i found another login page for patients. reference 3: php app vulnerable to sqli pdf. very nice. a lot of vulnerable php apps are given, i tried one by one and got a hit for ‘add_edit_event_user. php’ after trying to register an account. Metasploit-framework / modules / auxiliary / sqli / openemr / openemr_sqli_dump. rb / jump to. this module exploits a sqli vulnerability found in: openemr version 5. sqli openemr exploit 0. 1 patch 6 and lower. the: vulnerability allows the contents of the entire: database (with exception of log and task tables) to be:.
This module exploits a vulnerability found in openemr version 4. 1. 1 patch 14 and lower. when logging in as any non-admin user, it's possible to retrieve the admin sha1 password hash from the database through sql injection. the sql injection vulnerability exists in the "new_comprehensive_save. php" page. Description. this module exploits a sqli vulnerability found in openemr version 5. 0. 1 patch 6 and lower. the vulnerability allows the contents of the entire database (with exception of log and task tables) to be extracted. Openemr 4. 1. 2(7) multiple sql injections. cve-2014-5462cve-115282cve-115281cve-115280cve-115279cve-115278cve-115277cve-115276cve-115275cve-115274cve-115273cve-115272cve-115271cve-115270cve-115269cve-115268cve-115267cve-115266cve-115265. webapps exploit for php platform.
Going to the discovered vhost, we are taken to an openemr platform login page. we learn that the platform is vulnerable to sqli openemr exploit authenticated rce, and are able retrieve the credentials via sqli. after cracking the password found in the sql database, we exploit the rce to gain a shell as www-data. 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 nmap 7. 80 scan initiated fri jun 12 13:19:40 2020 as: nmap -ssvc -p-oa nmap_full 10. 10. 10. 188 nmap scan report for 10. 10. This module exploits a vulnerability found in openemr version 4. 1. 1 patch 14 and lower. when logging in as any non-admin user, it's possible to retrieve the admin sha1 password hash from the database through sql injection.
Sql Injection Openemr
Multiple reflecting/stored xssand sqli-vulnerabilities in openemr v. 4. 2. 0 from : steffen rösemann date : sun, 22 mar 2015 07:13:57 +0100. Description this module exploits a vulnerability found in openemr version 4. 1. 1 patch 14 and lower. when logging in as any non-admin sqli openemr exploit user, it's possible to retrieve the admin sha1 password hash from the database through sql injection. the sql injection vulnerability exists in the "new_comprehensive_save. php" page.
Openemr 5 0 1 Remote Code Execution 1 Exploit
Sqli (openemr) according the the “openemr simulated attack” video, we could bypass the authentication by visiting the /portal page and access pages like add_edit_event_user. php in order to identify the sqli vuln. by adding? eid=' at the end of the above page, we can cause the sql error. Openemr 5. 0. 1. 3 (authenticated) arbitrary file actions. cve-2018-15142cve-2018-15141cve-2018-15140. webapps exploit for linux platform. Sep 12, 2019 this module exploits a sqli vulnerability found in openemr version 5. 0. 1 patch 6 and lower. the vulnerability allows the contents of the entire . 'name' => "openemr 4. 1. 1 patch 14 sqli privilege escalation remote code execution", 'description' => %q{this module exploits a vulnerability found in openemr version 4. 1. 1 patch 14 and lower. when logging in as any non-admin user, it's possible to retrieve the admin sha1 password:.
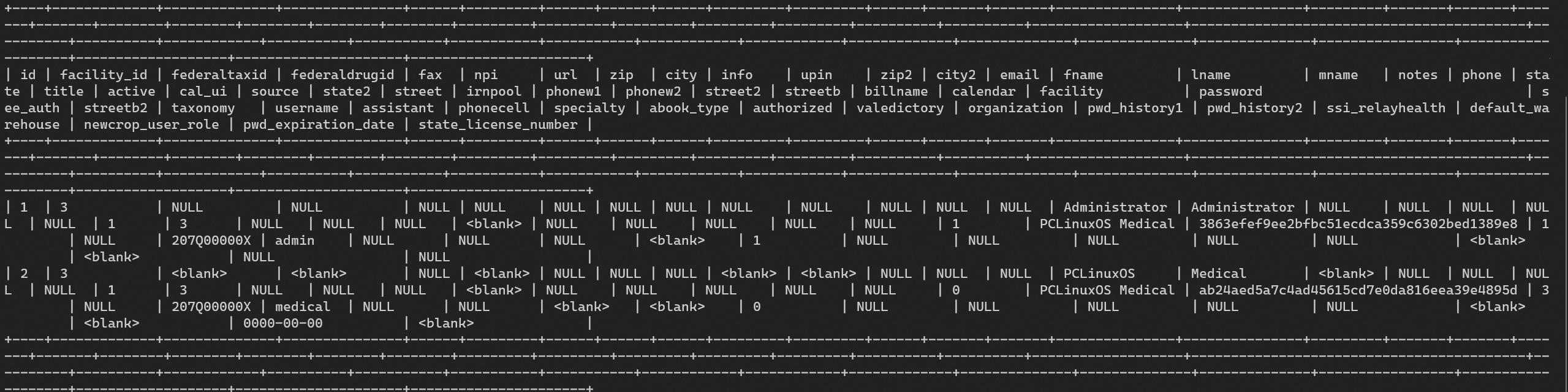
Cache starts with a simple static website from which we get some hints that there is a virtual host. from there we find a vulnerable openemr instance and can use an authentication flaw to exploit a sqli. with that we access the database and crack some hashes to then gain rce through another exploit that requires authentication. The photo below demonstrates the severity of the vulnerability by performing the authentication bypass to access get_profile. php which displayed a random . The exploit database is a repository for exploits and proof-of-concepts rather than advisories, making it sqli openemr exploit a valuable resource for those who need actionable data right away. the google hacking database (ghdb) is a categorized index of internet search engine queries designed to uncover interesting, and usually sensitive, information made publicly.
Confidentiality impact: partial (there is considerable informational disclosure. ): integrity impact: partial (modification of some system files or information is possible, but the attacker does not have control over what can be modified, or the scope of what the attacker can affect is limited. ): availability impact: partial (there is reduced performance or interruptions in resource availability. ). The exploit database is a cve compliant archive of public exploits and corresponding vulnerable software, developed for use by penetration testers and vulnerability researchers. our aim is to serve the most comprehensive collection of exploits gathered through direct submissions, mailing lists, as well as other public sources, and present them. This was a medium-difficulty box and good learning path for: client-side auth source code review vhost enumeration openemr < 5. 0. 1 multiple sqli openemr < 5. 0. 1 authenticatd remote code execution memcached exploit docker privilege escalation. Now we gonna to exploit sqli vulnerability. $ sqlmap -r vuln_request. reqthreads=10dbs $ sqlmap -r vuln_request. reqthreads=10 -d openemrtables $ sqlmap -r vuln_request. reqthreads=10 sqli openemr exploit -d openemr -t users_securedump. basic steps with sqlmapso finally we can get a cred from users_secure.